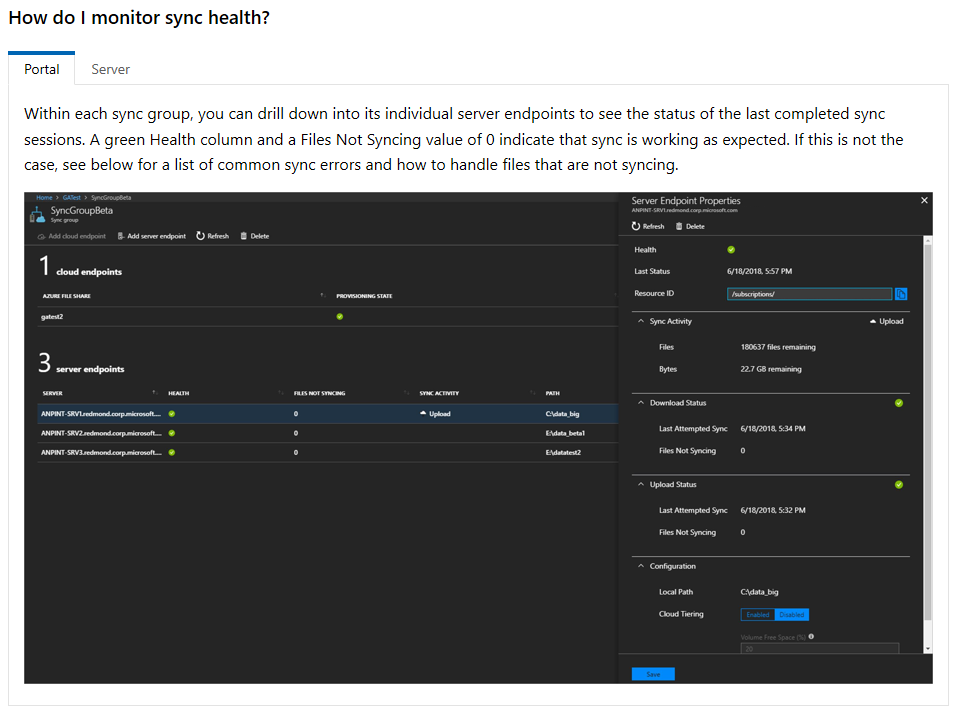
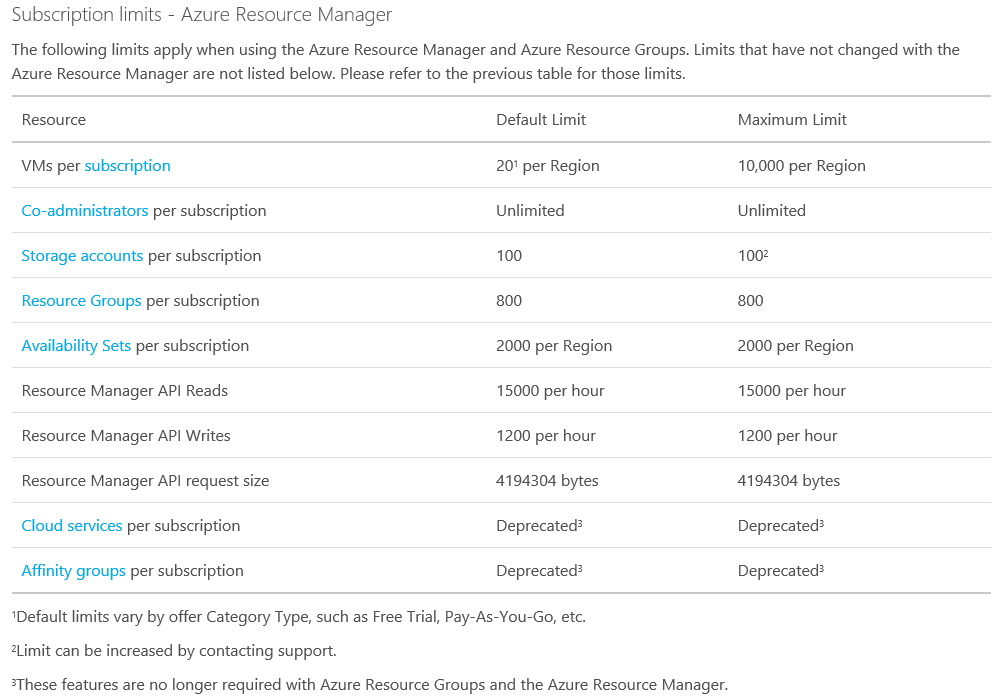
Best practices to architect Resource Groups in Azure

On a workshop at the client, we were talking about what are the best practices to design an architecture for Resource Groups (RG) in Azure. This time we have a good time debating what will be the scenarios and what...