Monitoring Azure File Sync
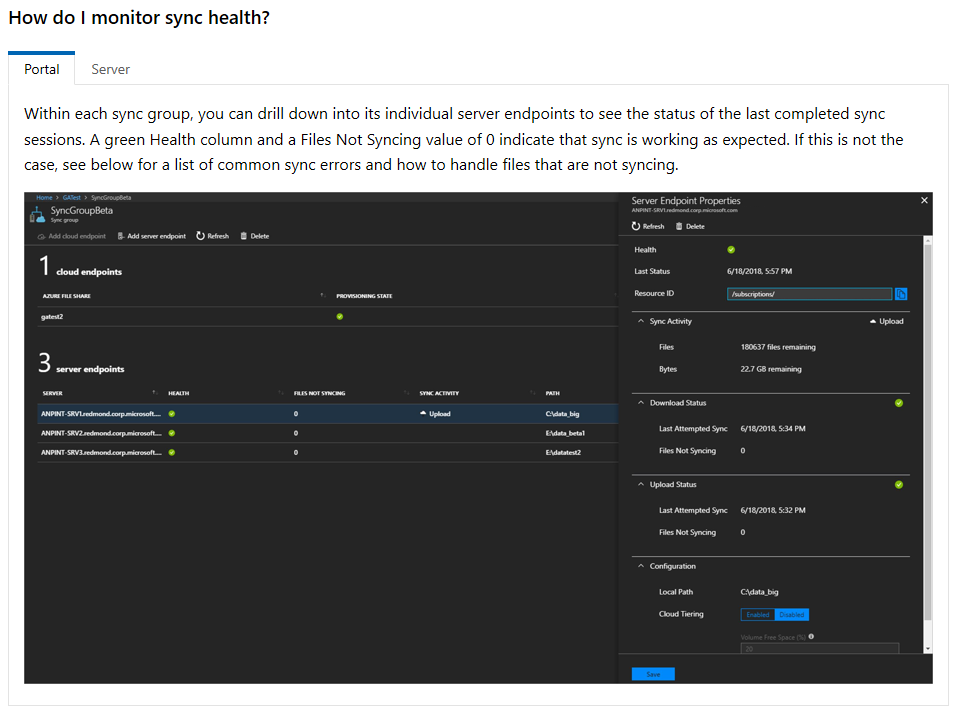
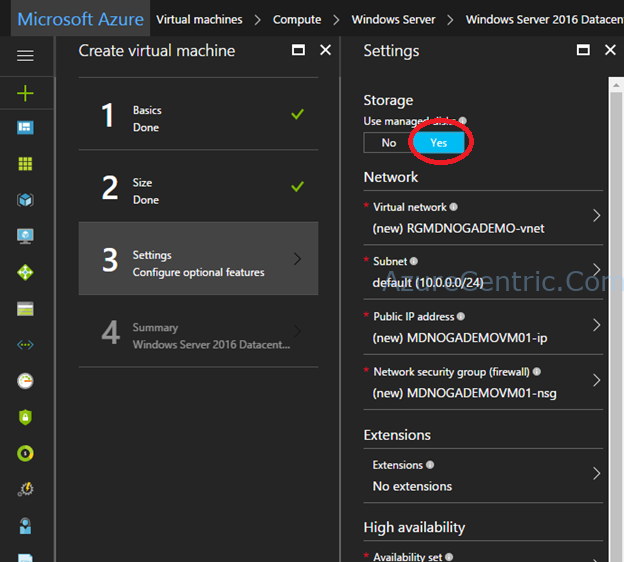
After implementing Azure File Sync, you wonder, how I can monitor what I just implemented? My first thought was to investigate in the Azure Resource himself, to look the sync service and see whether there are any diagnostics settings which...