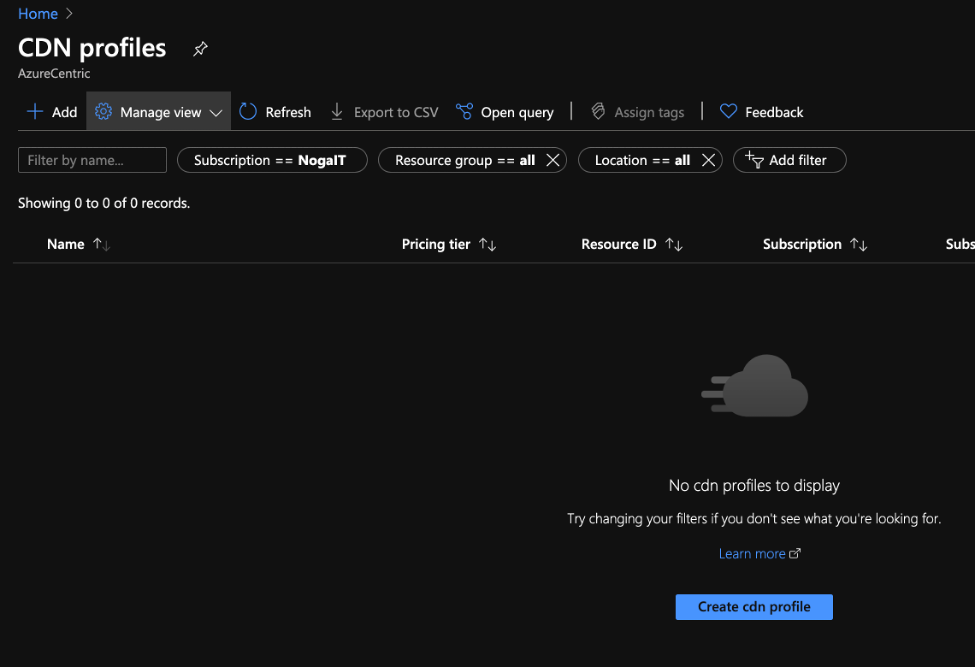
Today I was creating an Azure CDN Profile, so I could deploy static content across different azure regions. So, I went to Azure Portal I start the process. First step is to create the CDN Profile. In this case I never use the CDN on this subscription, as you can see from the picture bellow.
Error on creating an Azure CDN profile with Resource Provider