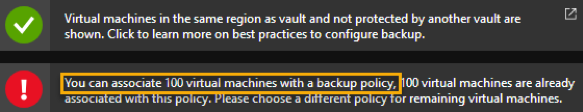
Azure Spot Virtual Machines
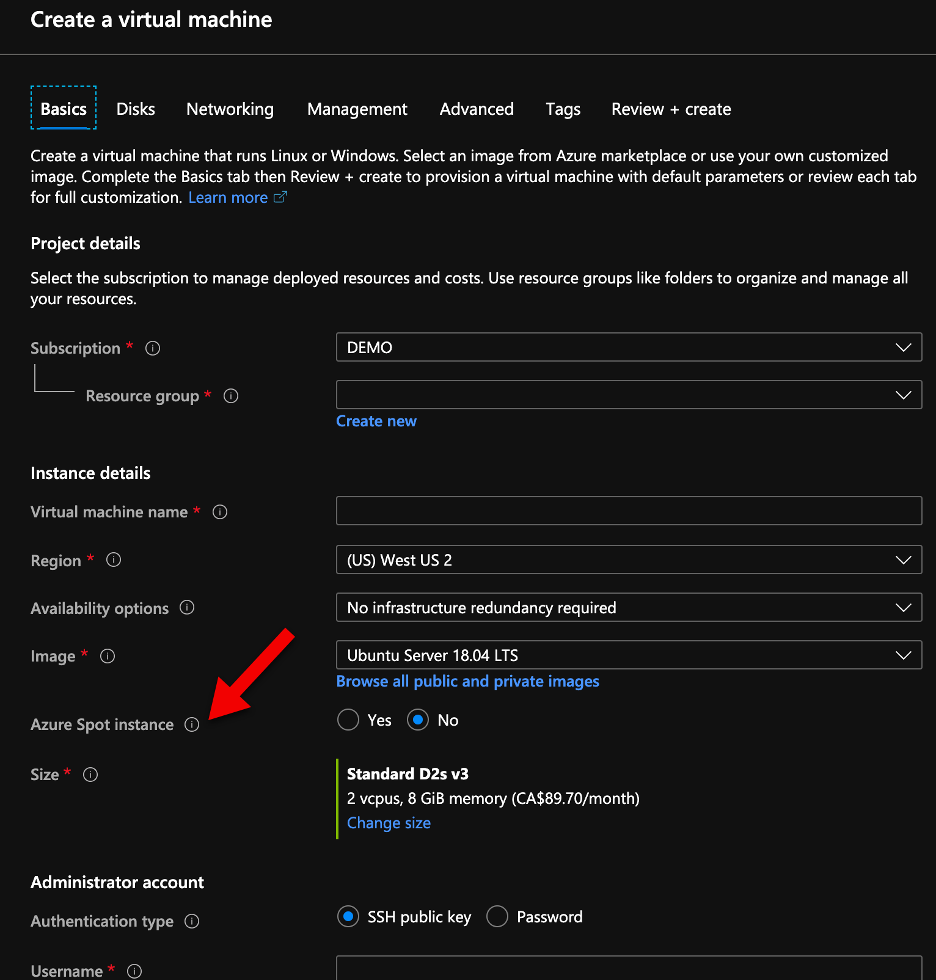
Today Microsoft announced the general availability of Azure Spot VMs (see here the announcement). This is one of the features that I have been waiting to become general available and start to use on my costumers.