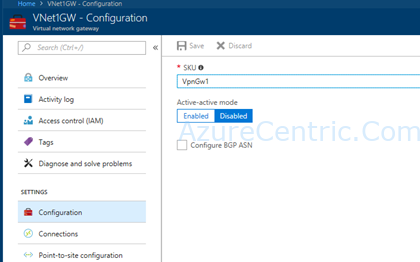
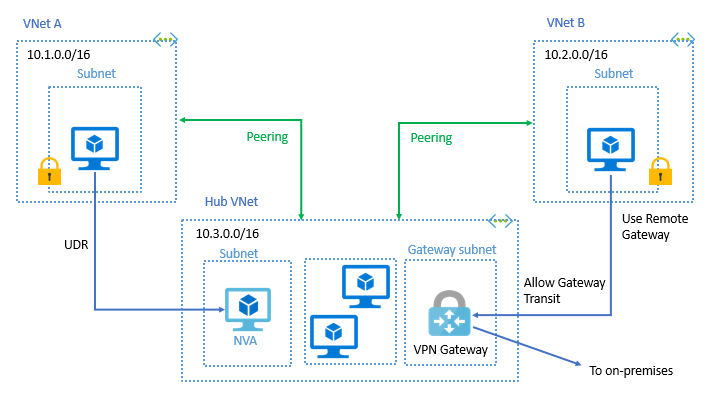
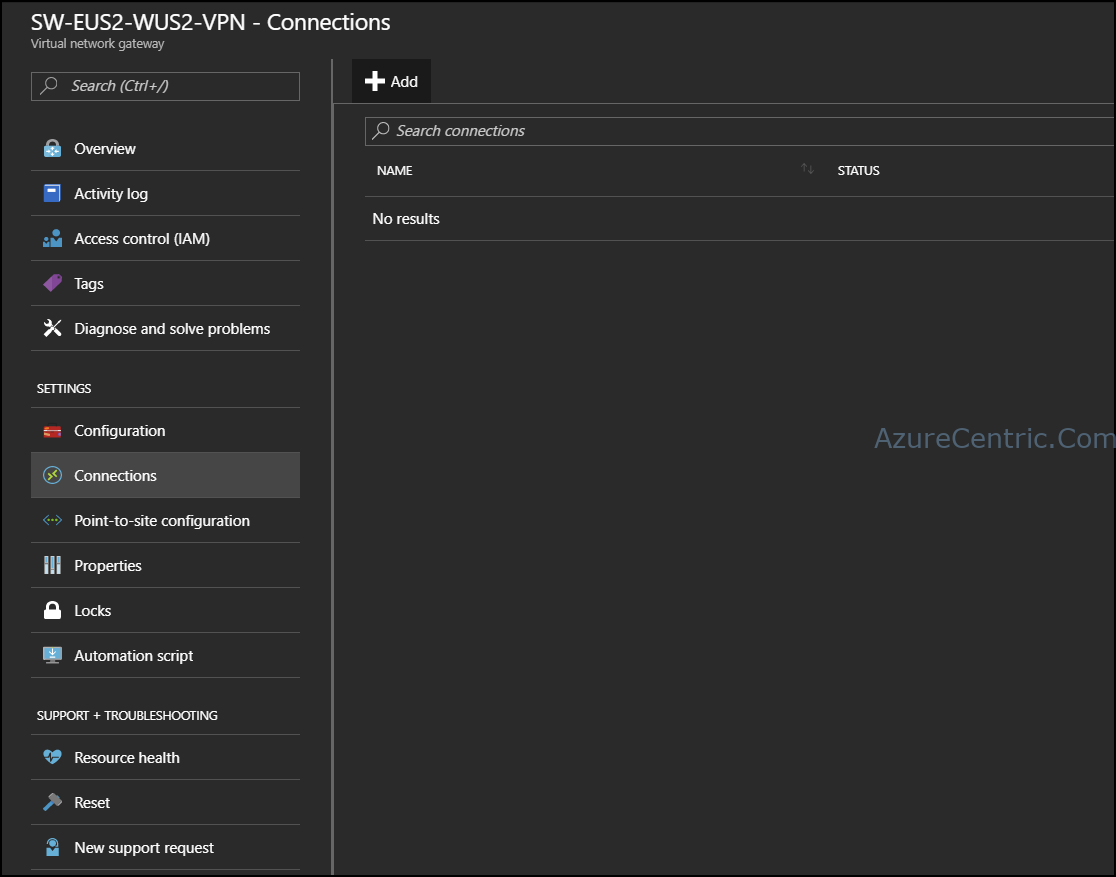
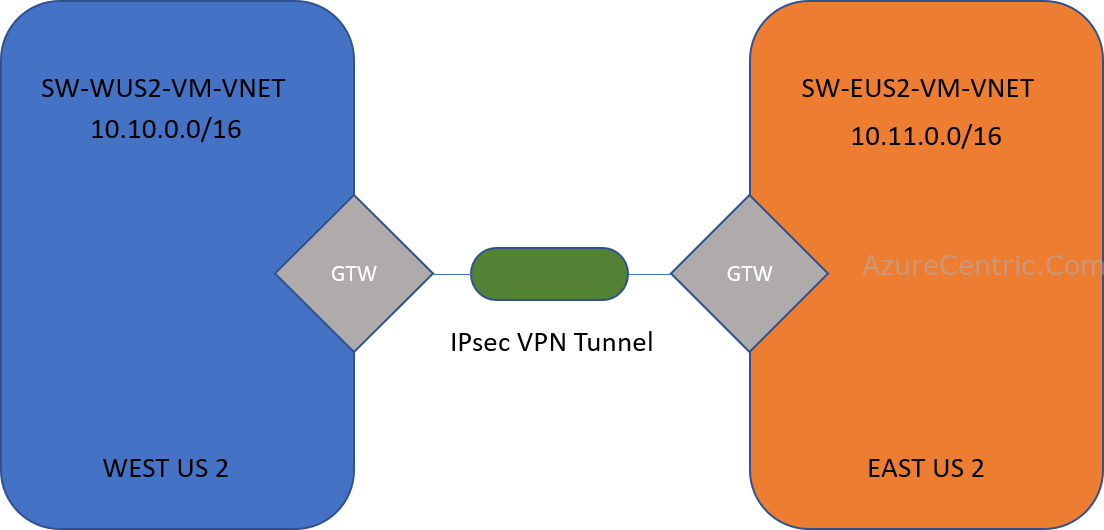
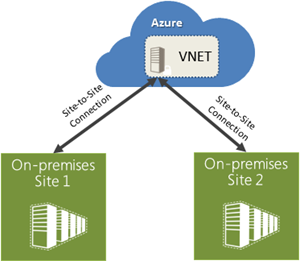
Infrastructure as a Code (IaC) Series #1 – The beginning!

From the past months, I’ve been upgrading all my scripts that I have been using along the years to a platform that allows me to be more productive, reusing all the IP that I have been gathering and creating along...